Environment Members
Each AutoMQ environment can be independently accessed, with a separate account system within each environment to manage the resources.- Environment members are completely isolated between different environments to prevent confusion and permission leaks.
- Environment members are not associated with cloud provider accounts and are mutually independent.
Initial Environment Members
Referencing the Overview▸, when an environment is created for the first time, the system automatically initializes and creates an Admin role member for the current environment.The initial Admin member’s username is admin, and the default password varies depending on the cloud provider environment. It is recommended to change the initial default password after logging in.
- Deploy using Alibaba Cloud Service Nest
- Deploy using Docker
In the Alibaba Cloud environment, use the Cloud Marketplace (Compute Nest) to deploy the BYOC environment. After deployment, go to the Compute Nest Console Service Instances > My Service Instances > Private Deployment Services to view the initial password.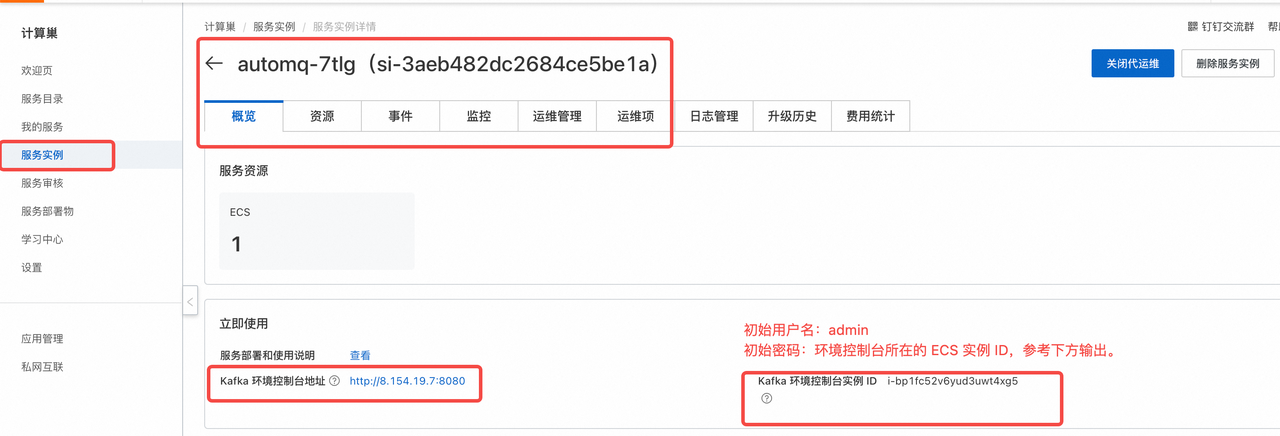

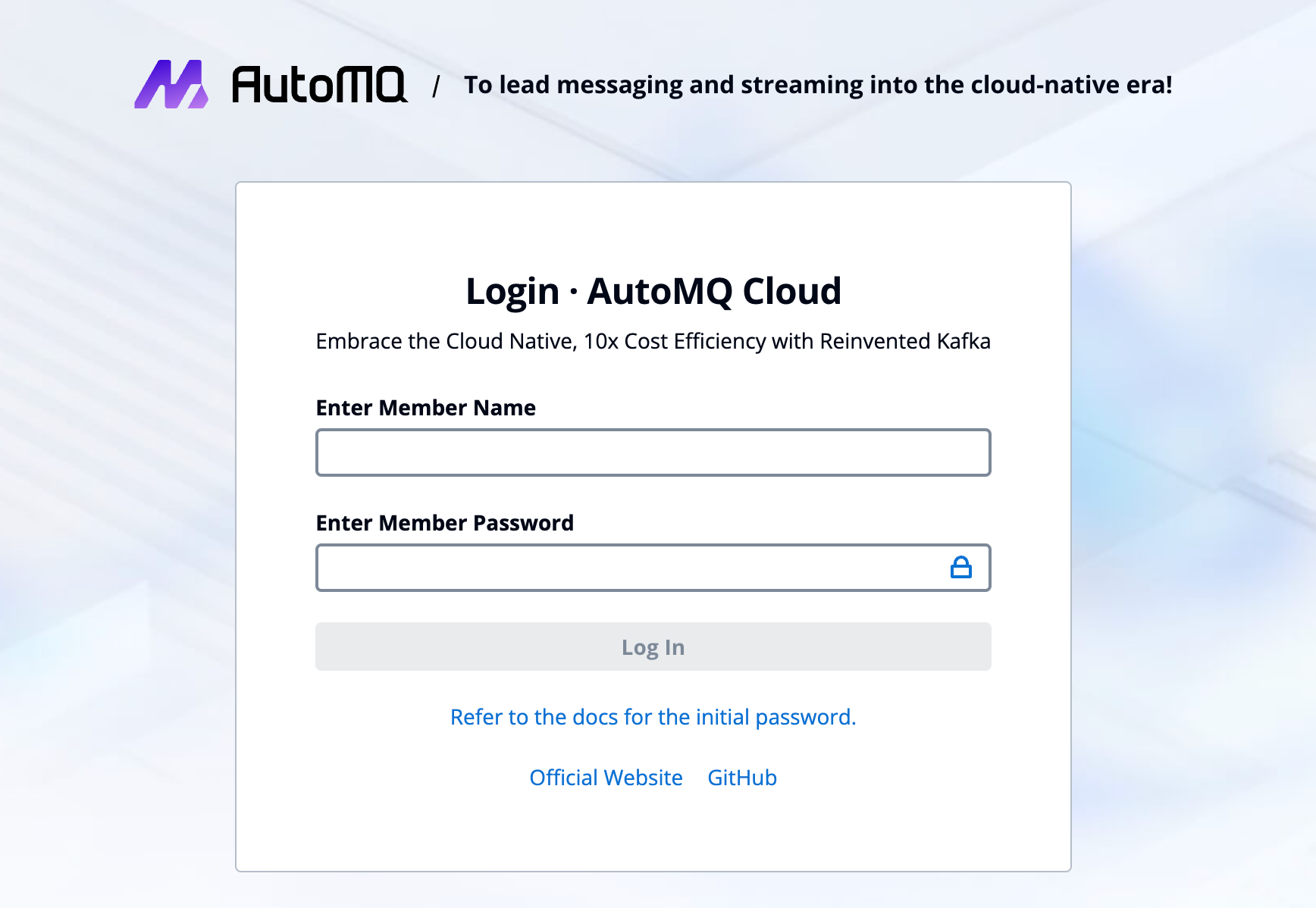
Login Environment
The environment administrator records the domain name of the environment console and distributes it to all environment members. Environment members can log in directly by entering their account information.- Open the environment console address in a browser. This address is provided by the environment administrator from the deployment system.
- Enter the environment member’s username and password to log in.
- For the first login, if using a system-generated password, it is recommended to change it to a custom password as soon as possible.
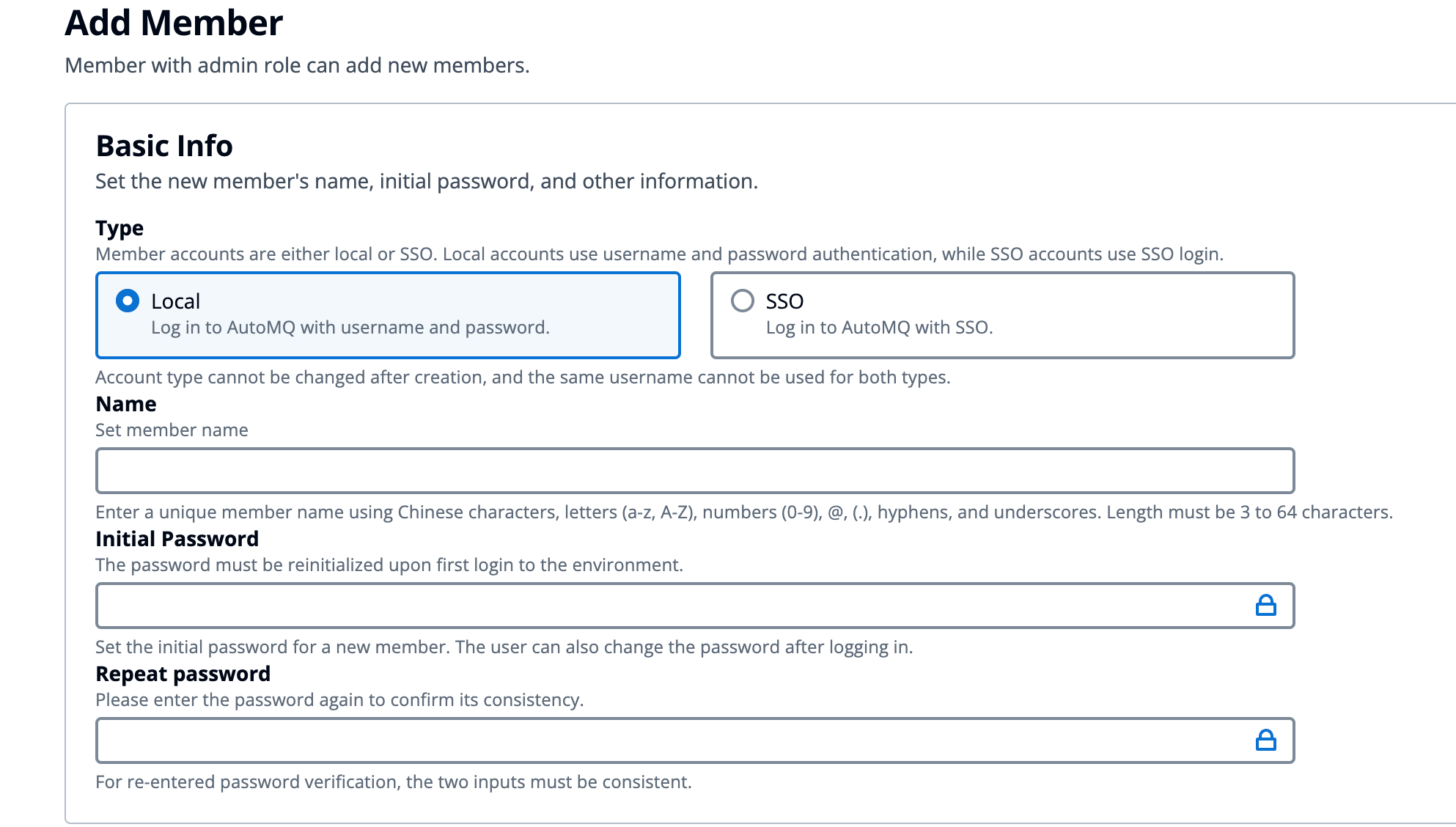
Create Environment Members
Using the AutoMQ Cloud environment console, environment members with the Admin role can create new member accounts to share the environment. The steps to create environment members are as follows:- Admin role environment members enter the environment.
- Click on the “Members” button in the left navigation bar to access the member list.
-
Click “Add Member,” select the type of member account, enter the member’s username, choose the role to assign, and click “Add.”
- Local Type: The local type is the default member account type, using a static username and password for login authentication.
- SSO Type: The SSO type needs to cooperate with an enterprise identity service provider, using SSO for login, and does not support username and password login.
- The system will return the new member’s username and default password.