Skip to main contentAutoMQ provides at-rest encryption for application data, ensuring that data encryption is fully transparent to the user’s application and is facilitated through the cloud vendor’s storage services. This document outlines the steps to configure at-rest data encryption.
Operation Principle
In AutoMQ’s BYOC service, data storage is primarily divided into two categories:
-
Object Storage: This service is utilized for storing message data, system logs, metrics, and other data types.
-
Block Storage: This service is employed for storing control plane metadata, such as Kafka KRaft, instances, and accounts.
Both types of storage services use transparent data encryption provided by cloud vendors to encrypt data at rest. Simply enable encryption of data at rest during the creation of the BYOC console and instance to achieve transparent encryption.
For more information on how cloud storage implements transparent encryption, you can refer to the following:
Usage Restrictions:The encryption keys for AutoMQ BYOC service storage are managed by the cloud vendor, and BYOK (Bring Your Own Key) custom keys are not currently supported.The data encryption feature is currently only supported on AWS, and adaptation for other cloud vendor environments is in progress. If needed, please contact us via Obtaining Services▸. Configuration Instructions
When enabling end-to-end static data encryption, follow the steps outlined below. It’s important to enable this feature both during the creation of a BYOC environment console and when setting up an instance. Please note that making changes to existing environment consoles or instances is not yet supported.
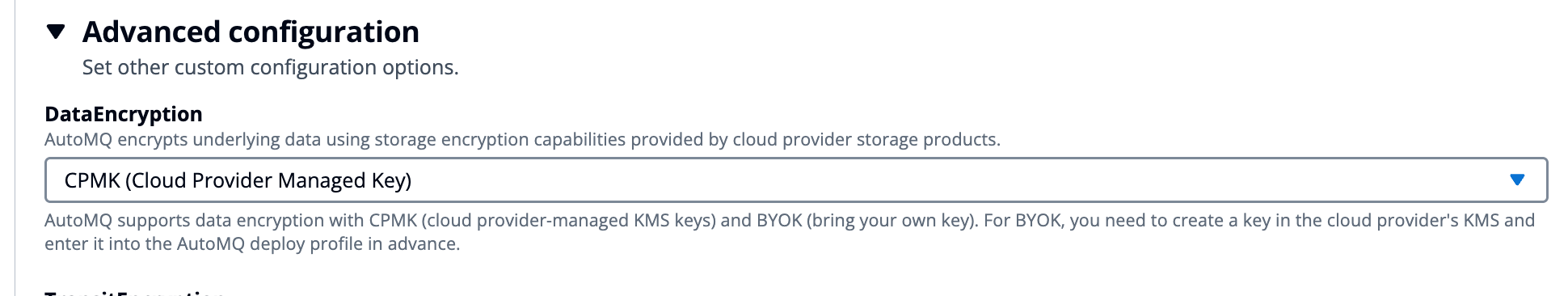
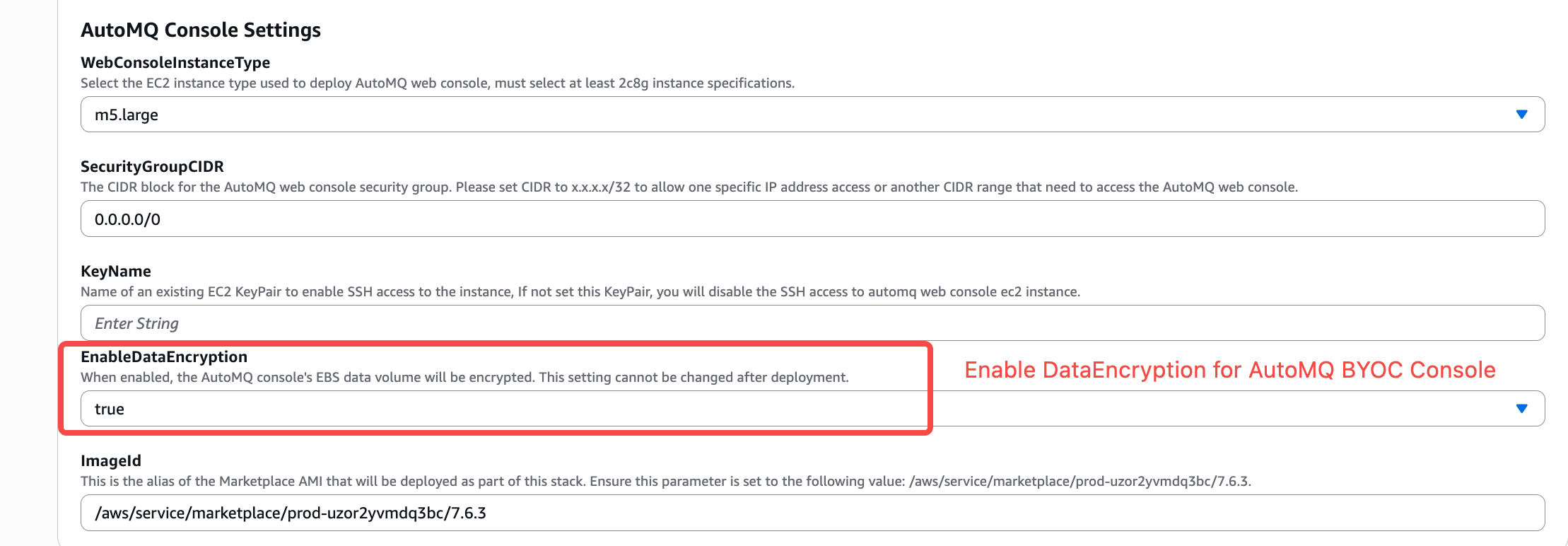
- When creating a BYOC console, enable the DataEncryption option.
- When creating an instance, click on advanced options and enable DataEncryption.