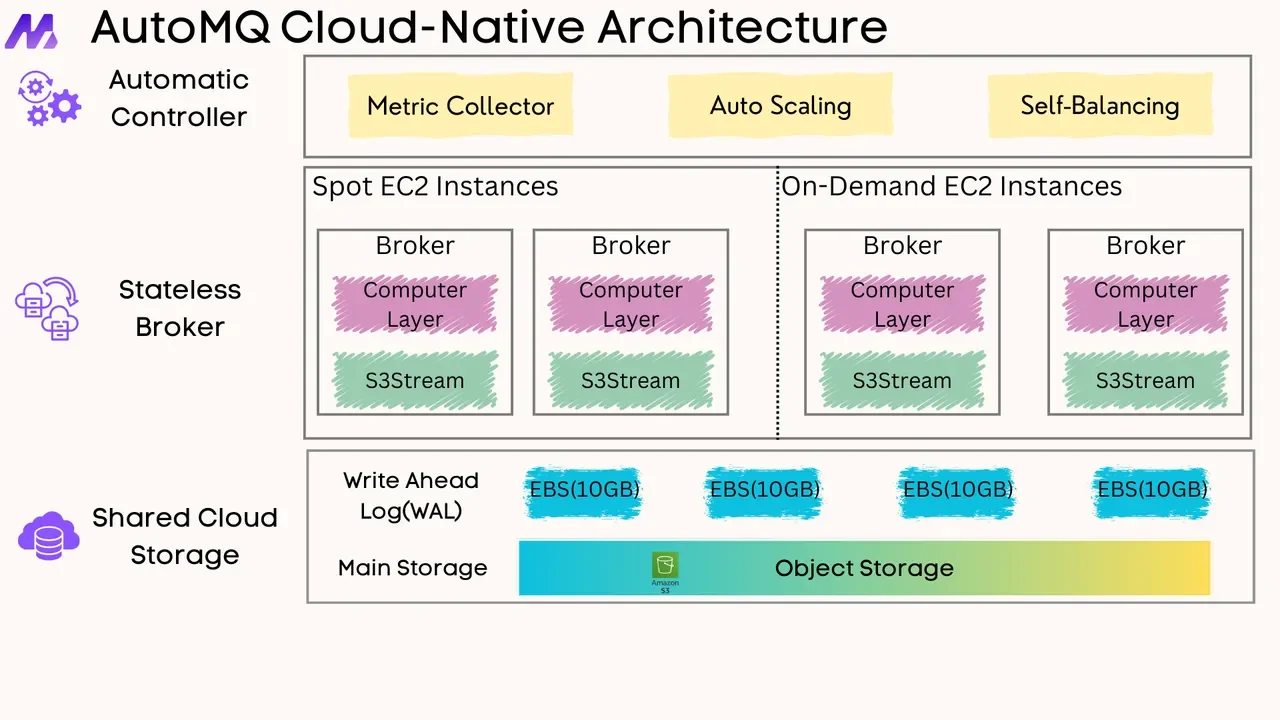
Overview
For a long time, managing IT infrastructure meant a lot of manual work. Think system administrators physically setting up servers, manually configuring networks, and painstakingly installing software. This is what we call Traditional Infrastructure Management . But as technology evolved, especially with the rise of the cloud, a new, more efficient method emerged: Infrastructure as Code (IaC) .
This blog will explore both approaches, compare them side-by-side, and delve into the world of IaC, including its benefits, best practices, and common challenges.
What is Traditional Infrastructure Management?
Traditional Infrastructure Management relies heavily on manual processes to design, build, deploy, and maintain IT infrastructure. This often involves:
-
Manual Provisioning: IT teams would order physical servers, wait for them to arrive, then manually rack them, connect cables, and install operating systems and necessary software. For network devices like routers and switches, engineers would log in via Command Line Interfaces (CLIs) to configure settings such as VLANs and routing protocols.
-
Manual Configuration: Configurations were often done through graphical user interfaces (GUIs) or CLIs on individual devices. This could lead to "snowflake servers" – servers with unique, undocumented configurations that are hard to reproduce or troubleshoot .
-
Ticket-Based Workflows: Changes were typically initiated through a ticketing system. An engineer would pick up a ticket, manually perform the requested changes, and then close the ticket. This process, while offering control, could be slow and create bottlenecks.
-
Tools: Common tools included vendor-specific GUIs, CLIs (like Cisco IOS or Juniper Junos for network devices), custom scripts for small automation tasks, and monitoring tools like Nagios or Zabbix to keep an eye on system health.
While this method offers direct control, it's often slow, error-prone, difficult to scale, and can lead to inconsistencies across environments.
![Infrastructure Management Components [9]](/blog/infrastructure-as-code-iac-vs-traditional-infrastructure-management/1.png)
What is Infrastructure as Code (IaC)?
Infrastructure as Code (IaC) is the practice of managing and provisioning IT infrastructure through machine-readable definition files (code), rather than manual hardware configuration or interactive configuration tools . Essentially, you write code to define what your servers, networks, storage, and other infrastructure components should look like, and an IaC tool takes care of making it happen.
Core Concepts of Infrastructure as Code:
-
Declarative vs. Imperative:
-
Declarative: You define the desired state of your infrastructure, and the IaC tool figures out how to achieve it. Tools like Terraform and AWS CloudFormation are primarily declarative . For example, you declare you need a web server with specific characteristics, and the tool handles the provisioning and configuration steps.
-
Imperative: You define the specific commands or steps needed to reach the desired state. Tools like Ansible and Chef can operate in an imperative way . For example, you write a script that executes a series of commands to install and configure a web server.
-
-
Idempotence: This is a crucial principle in IaC. It means that applying the same configuration multiple times produces the same result, without unintended side effects . If you run your IaC script again, it won't create a new server if one with the defined configuration already exists; it will ensure the existing one matches the defined state.
-
Version Control: IaC files are treated like application source code. They are stored in version control systems like Git. This allows teams to track changes, collaborate effectively, revert to previous stable configurations if something goes wrong, and maintain an audit trail .
-
Automation: IaC automates the entire infrastructure lifecycle, from provisioning to configuration and decommissioning. This significantly reduces manual effort and speeds up deployments .
How Infrastructure as Code Works:
-
Define: You write code (e.g., in HCL for Terraform, YAML for Ansible, JSON/YAML for CloudFormation, or a general-purpose language like Python with Pulumi) describing your infrastructure resources and their configurations .
-
Version: You commit this code to a version control system (e.g., Git) .
-
Deploy: An IaC tool reads your code and interacts with the underlying platform (e.g., a cloud provider like AWS, Azure, or GCP, or on-premises hypervisors) to provision and configure the resources as defined.
-
Manage State (for some tools): Some tools, like Terraform, maintain a "state file" that keeps track of the current infrastructure. This helps the tool understand what resources it manages and how they map to your code .
-
Update/Modify: To change your infrastructure, you modify the code, test it, and then re-deploy. The IaC tool intelligently applies only the necessary changes to reach the new desired state.
![Infrastructure as Code Pipeline [8]](/blog/infrastructure-as-code-iac-vs-traditional-infrastructure-management/2.png)
The Infrastructure as Code Lifecycle:
While not always explicitly a rigid set of steps, the lifecycle of infrastructure managed by IaC typically mirrors software development practices and can be seen as :
-
Plan: Define infrastructure requirements.
-
Code: Write infrastructure definitions in configuration files.
-
Build/Provision: Use IaC tools to create the infrastructure.
-
Test: Validate the infrastructure configurations.
-
Release/Deploy: Roll out the infrastructure.
-
Operate/Manage: The infrastructure is live and serving its purpose.
-
Monitor: Continuously monitor for performance, availability, and drift.
-
Update/Patch: Modify code to update configurations or apply patches.
-
Decommission: Remove infrastructure by updating or removing its definition in code.
Side-by-Side Comparison: Infrastructure as Code vs. Traditional
| Feature | Traditional Infrastructure Management | Infrastructure as Code (IaC) |
|---|---|---|
| Speed & Agility | Slow; manual provisioning takes days/weeks | Fast; automated provisioning in minutes/hours |
| Consistency | Prone to "snowflake servers" & drift | High consistency; defined by code |
| Scalability | Difficult and slow to scale manually | Easily scalable by modifying code |
| Cost | Higher operational costs (manual labor) | Lower operational costs; optimizes resource use |
| Reliability/Errors | Higher risk of human error | Reduced errors due to automation & testing |
| Disaster Recovery | Slow, complex manual rebuilds | Faster, repeatable DR via code |
| Security & Compliance | Manual checks, harder to audit | Codified policies, automated checks, audit trails |
| Version Control | Typically none or manual documentation | Full version control, rollback capabilities |
| Skills Required | Manual system admin skills | Coding, tool-specific knowledge, DevOps mindset |
| Collaboration | Siloed, ticket-based handoffs | Enhanced collaboration (Dev & Ops) via code |
Advantages of Infrastructure as Code
Transitioning to IaC offers significant benefits:
-
Automation: Reduces manual effort, freeing up engineers for more strategic tasks.
-
Speed & Efficiency: Drastically accelerates provisioning and deployment cycles.
-
Consistency & Standardization: Ensures every environment is provisioned the same way, reducing configuration drift.
-
Scalability: Makes it easy to scale infrastructure up or down on demand.
-
Cost Savings: Optimizes resource usage and reduces manual labor costs .
-
Version Control & Auditability: Provides a clear history of changes and enables easy rollbacks .
-
Improved Reliability: Minimizes human error through automation.
-
Enhanced Security: Allows security policies to be codified and consistently applied.
-
Better Collaboration: Fosters closer collaboration between development and operations teams (DevOps).
-
Disaster Recovery: Enables quicker and more reliable recreation of infrastructure in a DR scenario.
Challenges and Disadvantages of Infrastructure as Code
Despite its advantages, IaC also comes with challenges:
-
Learning Curve: Requires new skills, including coding and familiarity with IaC tools and concepts.
-
Initial Setup Complexity: Setting up IaC pipelines and choosing the right tools can be complex and time-consuming.
-
State Management: Managing the state file (for tools like Terraform) can be tricky. Corruption or misconfiguration can lead to significant problems.
-
Secrets Management: Securely handling sensitive data like passwords and API keys within IaC configurations requires careful planning and dedicated tools.
-
Tool Sprawl: The variety of IaC tools can lead to choosing too many or the wrong ones for the job.
-
Configuration Drift (Still Possible): If manual changes are made to IaC-managed infrastructure outside the IaC process, drift can still occur, though tools can help detect it.
-
Error Propagation: An error in the IaC code can be rapidly propagated across many resources, potentially causing widespread issues if not caught in testing.
Popular Infrastructure as Code Tools
Several tools are available to implement IaC, each with its strengths:
-
Terraform: An open-source tool by HashiCorp that uses a declarative language (HCL). It's cloud-agnostic, supporting many providers, and manages infrastructure state .
-
Ansible: An open-source automation tool (often used for configuration management but also provisioning). It's agentless and uses YAML for its "playbooks" .
-
AWS CloudFormation: An AWS-specific service that allows you to model and set up your Amazon Web Services resources using JSON or YAML templates .
-
Azure Resource Manager (ARM) & Bicep: ARM templates (JSON) are Azure's native IaC solution. Bicep is a domain-specific language (DSL) that transpiles to ARM JSON, offering a simpler syntax .
-
Google Cloud Deployment Manager: GCP's native IaC service, using YAML for configuration and Python or Jinja2 for templates.
-
Pulumi: An open-source IaC tool that allows you to use familiar programming languages like Python, JavaScript, TypeScript, Go, and C# to define and deploy cloud infrastructure .
-
Chef: A configuration management tool that uses a Ruby-based DSL. It's often used for more complex configurations and typically employs an agent-based approach .
-
Puppet: Another established configuration management tool that uses a declarative, Ruby-based DSL. It's known for its strong modeling capabilities and often uses an agent/master architecture .
-
Salt (SaltStack): An open-source platform for event-driven IT automation, remote task execution, and configuration management. It's Python-based and can operate with or without agents (minions).
Best Practices for Implementing Infrastructure as Code
To make the most of IaC, consider these best practices:
-
Version Everything: Store all your IaC files in a version control system like Git .
-
Use Modules: Break down your infrastructure code into reusable, composable modules. This improves organization, maintainability, and reusability.
-
Test Your Code: Implement automated testing for your IaC. This can include linting, static analysis, unit tests, integration tests, and compliance tests.
-
Manage Secrets Securely: Do not hardcode secrets in your IaC files. Use dedicated secret management tools like HashiCorp Vault or cloud provider services (e.g., AWS Secrets Manager, Azure Key Vault).
-
Keep State Files Secure and Remote: For stateful IaC tools like Terraform, store state files securely in a remote backend that supports locking to prevent concurrent modifications.
-
Automate with CI/CD Pipelines: Integrate your IaC workflows into Continuous Integration/Continuous Delivery (CI/CD) pipelines to automate testing and deployment.
-
Monitor for Configuration Drift: Continuously monitor your infrastructure for any changes made outside of the IaC process and remediate them.
-
Iterate and Refactor: Treat your infrastructure code like application code. Refactor it regularly to improve clarity, efficiency, and maintainability.
-
Idempotency is Key: Ensure your scripts and configurations are idempotent .
-
Documentation: While IaC is self-documenting to an extent, provide clear comments and READMEs for complex configurations or modules.
Conclusion
While traditional infrastructure management laid the groundwork, Infrastructure as Code is clearly the way forward for modern IT operations. It brings the principles of software development – automation, versioning, testing, and collaboration – to infrastructure management. This results in faster deployments, greater consistency, improved reliability, and enhanced security.
Adopting IaC is a journey that requires changes in tools, processes, and culture, but the benefits in terms of agility and efficiency are well worth the investment.
If you find this content helpful, you might also be interested in our product AutoMQ. AutoMQ is a cloud-native alternative to Kafka by decoupling durability to S3 and EBS. 10x Cost-Effective. No Cross-AZ Traffic Cost. Autoscale in seconds. Single-digit ms latency. AutoMQ now is source code available on github. Big Companies Worldwide are Using AutoMQ. Check the following case studies to learn more:
-
Grab: Driving Efficiency with AutoMQ in DataStreaming Platform
-
Palmpay Uses AutoMQ to Replace Kafka, Optimizing Costs by 50%+
-
How Asia’s Quora Zhihu uses AutoMQ to reduce Kafka cost and maintenance complexity
-
XPENG Motors Reduces Costs by 50%+ by Replacing Kafka with AutoMQ
-
Asia's GOAT, Poizon uses AutoMQ Kafka to build observability platform for massive data(30 GB/s)
-
AutoMQ Helps CaoCao Mobility Address Kafka Scalability During Holidays
-
JD.com x AutoMQ x CubeFS: A Cost-Effective Journey at Trillion-Scale Kafka Messaging