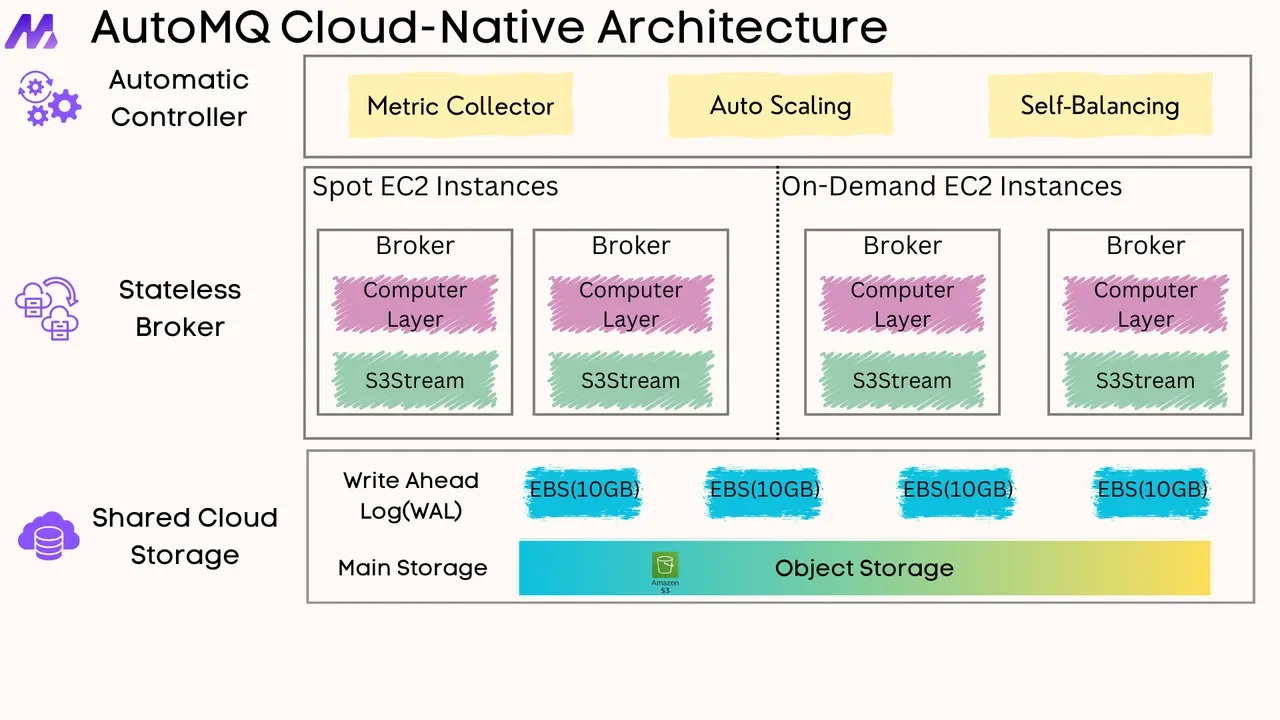
Overview
Apache Kafka has become the backbone of modern real-time data pipelines for countless organizations. Its ability to handle high-throughput, fault-tolerant stream processing is unparalleled. However, as Kafka adoption grows within an organization, a critical architectural decision emerges: should you opt for a multi-tenant Kafka setup or stick with single-tenant clusters?
Choosing the right model is crucial as it impacts cost, performance, security, and operational complexity. In this blog, we'll dive deep into both single-tenant and multi-tenant Kafka architectures, explore their pros and cons, and provide guidance on selecting the best fit for your needs.
Understanding Single-Tenant Kafka
What is it?
A single-tenant Kafka architecture means that a dedicated Kafka cluster (including brokers, and often its Zookeeper or KRaft controller nodes) serves a single customer, application, or team . Think of it as a private, standalone Kafka environment. All the resources of that cluster—CPU, memory, disk I/O, network bandwidth—are exclusively available to that one tenant.
How it Works
In this model, the tenant has full control over their Kafka environment. They can configure it, scale it, and manage it according to their specific requirements without worrying about interference from other applications or teams. This isolation is the hallmark of single-tenancy. Deployments can be on-premises, in a private cloud, or a dedicated setup within a public cloud provider .
Advantages of Single-Tenant Kafka:
-
Performance Predictability & Isolation: Since resources are not shared, the tenant experiences consistent and predictable performance. There's no "noisy neighbor" effect, where one tenant's heavy workload impacts others .
-
Enhanced Security & Data Segregation: Data is physically and logically isolated, which can be crucial for applications with stringent security and compliance requirements. The tenant has full control over security configurations .
-
Greater Customization: Tenants can fine-tune Kafka configurations, install specific plugins, or manage upgrade schedules according to their unique needs .
-
Simplified Fault Isolation: If an issue occurs, it's contained within that single-tenant environment, minimizing the "blast radius" . Troubleshooting can also be simpler.
Disadvantages of Single-Tenant Kafka:
-
Higher Cost: Running dedicated clusters for each tenant can be significantly more expensive due to the proliferation of resources (brokers, storage, compute) . This includes both infrastructure and licensing costs if applicable.
-
Increased Management Overhead: Each dedicated cluster needs to be provisioned, monitored, maintained, and upgraded independently. This requires more operational effort, especially as the number of tenants grows .
-
Resource Underutilization: Often, a single tenant may not fully utilize the capacity of their dedicated cluster, leading to wasted resources and inefficiencies. Planning for peak capacity can exacerbate this.
Typical Use Cases for Single-Tenant Kafka:
-
Large enterprise applications with very high throughput or strict performance SLAs.
-
Applications handling highly sensitive data requiring maximum security and isolation (e.g., certain financial or healthcare systems).
-
Teams needing specific Kafka configurations or custom plugins not suitable for a shared environment.
-
Environments where predictable performance and complete control are paramount, and cost is a secondary concern.
Understanding Multi-Tenant Kafka
What is it?
Multi-tenant Kafka refers to an architecture where a single Kafka cluster is shared by multiple tenants (users, applications, teams, or even different business units) . While the underlying infrastructure is shared, logical isolation is implemented to keep tenants separate and secure. The official Apache Kafka documentation notes that Kafka can be deployed as a multi-tenant solution .
![Cluster Multi-tenancy [27]](/blog/multi-tenant-kafka-vs-single-tenant-kafka-/1.png)
How it Works
Multi-tenancy in Kafka relies on a combination of Kafka's built-in features and operational best practices to ensure that tenants can coexist on a shared cluster without adversely affecting each other. This often involves sharing brokers, but logically partitioning data and access.
Key Isolation Mechanisms in Multi-Tenant Kafka:
-
Topic Naming Conventions & Namespaces: Using prefixes or a well-defined structure for topic names helps segregate data logically for different tenants (e.g.,
tenantA-orders,tenantB-inventory) . This is a foundational step for organizing resources. -
Authentication & Authorization (ACLs): Kafka’s Access Control Lists (ACLs) are critical. They define which users (principals) have permission to perform specific operations (read, write, create, describe, delete) on specific resources (topics, consumer groups, cluster) . Strong authentication (e.g., SASL) ensures tenant identity, and ACLs enforce what they can access.
-
Resource Quotas: Kafka allows administrators to set quotas on producer and consumer throughput (byte rates) and request processing rates . This prevents a single tenant from monopolizing cluster resources like network bandwidth or broker CPU, mitigating the noisy neighbor problem . Some managed Kafka services offer advanced, auto-tuning quotas that adapt to changing loads .
-
Network Segmentation (Optional): In some advanced setups, network policies can further isolate tenant traffic.
-
Virtual Clusters (via Third-Party Tools): Some third-party Kafka management tools and proxies offer "virtual cluster" capabilities. These create an abstraction layer over a physical cluster, giving each tenant a seemingly dedicated Kafka environment, simplifying management and enhancing isolation without deploying physically separate clusters .
Advantages of Multi-Tenant Kafka:
-
Cost-Effectiveness: Sharing infrastructure significantly reduces hardware, maintenance, and operational costs compared to running many single-tenant clusters. This is a primary driver for adopting multi-tenancy .
-
Improved Resource Utilization: Resources are pooled and shared among tenants, leading to higher overall utilization and less wastage .
-
Simplified Management (of Clusters): Managing a few large multi-tenant clusters can be operationally simpler than managing numerous small, dedicated ones, especially regarding upgrades and patching the core infrastructure .
-
Easier Data Sharing (Controlled): While tenants are isolated, it can be easier to facilitate controlled data sharing between tenants on the same cluster if required, by carefully adjusting ACLs.
Disadvantages of Multi-Tenant Kafka:
-
Noisy Neighbor Potential: Despite quotas, a misbehaving or unexpectedly high-load tenant can still impact the performance of others if quotas are not perfectly configured or if there are resource bottlenecks not covered by quotas (e.g., excessive metadata requests) .
-
Security Complexity: Configuring and managing ACLs, quotas, and security policies for many tenants can be complex and error-prone. A misconfiguration could lead to data breaches or unauthorized access . Regular audits are essential.
-
Operational Overhead (for Tenant Management): While cluster management might be simpler, tenant onboarding, permission management, and per-tenant monitoring add a layer of operational complexity .
-
Fault Isolation Challenges: A failure in a shared component (e.g., a broker) can potentially affect multiple tenants. The "blast radius" can be larger than in a single-tenant setup, though managed services often have robust fault isolation within their multi-tenant architectures.
-
Upgrade Coordination: Upgrading a shared cluster might require more careful planning and coordination with multiple tenants to minimize disruption.
Typical Use Cases for Multi-Tenant Kafka:
-
Organizations with many teams or applications needing Kafka access but not justifying dedicated clusters.
-
SaaS providers offering Kafka-based services to multiple customers .
-
Development and testing environments where resources can be shared efficiently.
-
Centralized data hub scenarios where various departments consume and produce data streams.
Single-Tenant vs. Multi-Tenant: A Side-by-Side Look
| Feature | Single-Tenant Kafka | Multi-Tenant Kafka |
|---|---|---|
| Resource Isolation | Complete physical & logical isolation | Logical isolation; shared physical resources |
| Performance Predictability | High; no noisy neighbors | Can be variable; risk of noisy neighbors |
| Cost | High (dedicated resources, ops) | Lower (shared resources, pooled ops) |
| Security & Data Segregation | Highest; full control | Depends on ACLs, quotas, encryption; more complex |
| Management Overhead | High (per cluster) | Lower (for core cluster); higher (for tenant mgmt) |
| Scalability & Elasticity | Scaled per tenant; may require overprovisioning | Easier to absorb varying loads; better elasticity |
| Customization | High; full environment control | Limited by shared nature; some tenant-level configs |
| Fault Isolation & Blast Radius | Excellent; contained to one tenant | Potentially larger blast radius; depends on architecture |
Key Considerations When Choosing Your Model
Selecting the right tenancy model isn't a one-size-fits-all decision. Consider these factors:
-
Workload Characteristics: Are your workloads highly variable or predictable? Do they have extreme performance demands?
-
Isolation Requirements: How critical is performance isolation? What are your security and compliance mandates for data segregation?
-
Budget & Cost Constraints: What is your budget for infrastructure and operational staffing? Multi-tenancy is generally more cost-effective for serving many distinct workloads.
-
Operational Capacity & Expertise: Do you have the team and expertise to manage many individual clusters (single-tenant) or the complexities of a secure, robust multi-tenant environment?
-
Scalability Needs: How quickly do you need to scale up or down? Multi-tenant systems can often offer better elasticity.
-
Number of Tenants/Applications: A few very large, critical applications might warrant single-tenant clusters. Many smaller applications are often better suited to a multi-tenant setup.
Best Practices for Single-Tenant Kafka
While single-tenant Kafka offers simplicity in terms of isolation, following best practices can help maximize its benefits and manage its drawbacks:
-
Right-Size Resources: Continuously monitor usage and adjust cluster resources (brokers, CPU, memory, storage) to match the tenant's actual needs. This helps control costs while ensuring performance.
-
Tailor Configurations Deeply: Leverage the complete control to fine-tune broker settings, topic configurations (partitions, replication factors), JVM parameters, and operating system settings specifically for the tenant's workload profile.
-
Implement Robust, Dedicated Monitoring: Set up comprehensive monitoring and alerting for the specific cluster. Track performance metrics, resource utilization, and potential bottlenecks closely.
-
Dedicated Security Hardening: Apply rigorous security measures tailored to the tenant. This includes network isolation, strong authentication mechanisms, and precise authorization, even if it’s a single logical tenant.
-
Optimize Hardware and Storage: Select hardware (CPU, memory, high-speed networking) and storage (e.g., SSDs for low-latency applications) that are best suited for the specific performance and reliability requirements of the tenant.
-
Automate Operations: Even for a single cluster, automate provisioning, configuration management, scaling operations, and routine maintenance tasks to reduce manual effort and ensure consistency.
-
Develop a Clear Upgrade Strategy: Plan and test Kafka version upgrades carefully, taking advantage of the isolated environment to schedule them at times that minimize impact on the tenant.
-
Implement Tenant-Specific Backup and DR: Design and implement backup and disaster recovery strategies that meet the recovery time objectives (RTO) and recovery point objectives (RPO) for that specific tenant’s data and applications.
-
Clear Cost Management: Ensure clear visibility and management of the costs associated with the dedicated cluster, attributing them accurately to the tenant.
Best Practices for Multi-Tenant Kafka
If you opt for a multi-tenant architecture, implementing these best practices is crucial:
-
Implement Strong Authentication & Authorization: Use SASL for authentication. Define granular ACLs following the principle of least privilege .
-
Enforce Resource Quotas: Set appropriate producer/consumer byte-rate quotas and request-rate quotas to prevent resource abuse and ensure fair sharing . Some systems, like the one used at LINE, found request quotas more critical than byte-rate quotas for certain workloads .
-
Standardize Topic Naming Conventions & Namespaces: Implement a clear, enforced topic naming strategy that includes tenant identifiers to logically separate data and simplify ACL management .
-
Monitor Extensively: Monitor key cluster metrics and, where possible, per-tenant resource usage (throughput, request rates, errors). Research into self-tuning multi-tenant Kafka highlighted the importance of monitoring request queue sizes and dynamically adjusting quotas .
-
Consider Chargeback/Showback: For internal tenants, implement mechanisms to track resource consumption per tenant for showback or chargeback, promoting responsible usage . This often involves tagging topics or clients with tenant identifiers and using metrics systems to aggregate usage.
-
Automate Tenant Provisioning: Automate the creation of topics, ACLs, and quotas for new tenants to reduce manual effort and ensure consistency.
-
Regularly Audit Security Configurations: Periodically review ACLs and security settings to ensure they remain appropriate and haven't been inadvertently relaxed.
Conclusion: Which Path to Choose?
The decision between single-tenant and multi-tenant Kafka hinges on balancing isolation, performance, cost, and operational complexity.
-
Choose Single-Tenant if: You have a few critical applications with extreme performance/security needs, require deep customization, and have the budget and operational capacity for dedicated environments.
-
Choose Multi-Tenant if: You need to serve many applications/teams cost-effectively, can manage the complexities of tenant isolation, and aim for higher resource utilization and operational efficiency for the underlying Kafka infrastructure.
Many organizations start with single-tenant clusters for initial critical workloads and then explore multi-tenancy as Kafka usage expands to achieve better economies of scale. Some may even adopt a hybrid approach, with critical, sensitive, or highly demanding workloads on dedicated clusters and other workloads on shared, multi-tenant clusters.
Regardless of the model, a deep understanding of Kafka's security features, resource management capabilities, and operational best practices is key to running a stable and efficient event streaming platform.
If you find this content helpful, you might also be interested in our product AutoMQ. AutoMQ is a cloud-native alternative to Kafka by decoupling durability to S3 and EBS. 10x Cost-Effective. No Cross-AZ Traffic Cost. Autoscale in seconds. Single-digit ms latency. AutoMQ now is source code available on github. Big Companies Worldwide are Using AutoMQ. Check the following case studies to learn more:
-
Grab: Driving Efficiency with AutoMQ in DataStreaming Platform
-
Palmpay Uses AutoMQ to Replace Kafka, Optimizing Costs by 50%+
-
How Asia’s Quora Zhihu uses AutoMQ to reduce Kafka cost and maintenance complexity
-
XPENG Motors Reduces Costs by 50%+ by Replacing Kafka with AutoMQ
-
Asia's GOAT, Poizon uses AutoMQ Kafka to build observability platform for massive data(30 GB/s)
-
AutoMQ Helps CaoCao Mobility Address Kafka Scalability During Holidays
-
JD.com x AutoMQ x CubeFS: A Cost-Effective Journey at Trillion-Scale Kafka Messaging